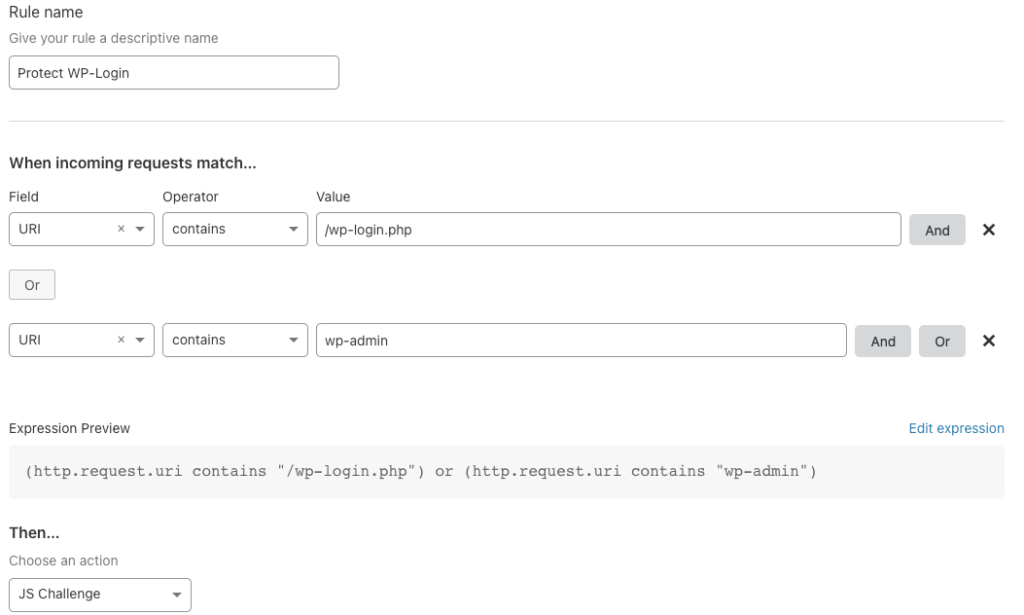
5G, the technology of the future.. or so we have been promised. Sadly that future is not upon us yet. Both T-Mobile and Verizon Wireless advertise lower latency, higher reliability, and faster speeds when using 5G over the previous generation LTE. Yet, some users of 5G see little improvement over the previous generation… What gives?
What is 5G?
5G stands for 5th-generation, referring to the fifth iteration of cellular technology. You may be familiar with 3G, and its more favored successor, 4G LTE. The fifth-generation was developed to answer for problems of ever-increasing network demand in the connected world. 5G adds some privacy, security, and performance features not available in 4G LTE.
The three flavors of 5G
You may have noticed how slow your cellular network gets when a nearby event occurs or when visiting stadiums and concerts. This occurs because a large number of users are connected to a single cell tower, slowing it down. LTE has issues with large groups connecting to a single tower because of the limitation of bandwidth available to transmit across and the way the underlying technology operates.
5G solves this specific issue using the mmWave high-band. The high-band operates roughly ten-times faster than LTE and can support a massive amount of users per tower. However, there are a few drawbacks. Thanks to our friend physics, these millimeter-size radio waves can’t penetrate buildings or travel far and pretty much require a line of sight and a nearby tower. The mmWave band is expected to be the best experience possible with 5G.
Opposite of mmWave high-band sits low-band 5G. Low-band is already deployed all over the United States by T-Mobile, Verizon, and is similar to LTE’s performance. The low-band allows for a much larger range and a slight performance boost (~20%) over LTE. For the next few years, the low-band is the best a majority of subscribers will experience. Cellular networks are currently utilizing low-band as the stepping stone for a better 5G.
The comprise of 5G is the mid-band. The mid-band is the ideal deployment nationwide by the cellular industry as it strikes a good balance between performance (~600% over LTE) and cost of deployment. Mid-band will require more deployments of cell-towers, but not nearly as much as the mmWave high-band would.
The ideal 5G puzzle
Piecing this three piece puzzle together creates the following setup:
- mmWave High-band:
Is expected to be placed in extremely populated areas, such as arenas, stadiums, downtown areas of large cities. This requires being nearly less than a couple of hundred feet from a high-band tower at any given time. - Mid-band:
Will be located across highways, population centers (cities, towns of all sizes), and suburban areas. The end goal is to have complete mid-band coverage, but that may be several years away. - Low-band:
Is to be located nearly everywhere the other two bands don’t exist. Think of this as the fall back where only a small amount of subscribers exist. This is the final piece to push LTE out of usage and will be increasingly uncommon to find over the next years. (Think of 3G now)
The current state of 5G
Many phone manufacturers are releasing support for 5G, but I don’t suggest upgrading only for 5G yet. T-Mobile (at the time of writing) has the largest deployment of l0w-band 5G. This deployment is nothing but impressive considering the given time-frame it occurred in, yet I wouldn’t read much into the hype.
Verizon still has the highest quality network hands down, yet doesn’t have as wide-spread 5G deployment. Should you consider switching? Probably not. In the end, 5G will only ever be as good as the network it is connected to.
The 5G experience now..
Through some independent testing of Verizon LTE customers, and T-Mobile 5G customers I often found that Verizon LTE customers received on average 20-30 Mbps faster speed than the T-Mobile 5G customers between customers who lived in the same rural and suburban regions. This comes down to the quality of the Verizon network, and the investments they have made into the quality of their LTE deployment. I expect that Verizon 5G customers will find more satisfaction out of their network as Verizon’s deployment rolls out further.
To explain this in simple terms, it is like buying a super expensive router on a slow internet connection. The router is great but doesn’t mean much for speed if the internet connection you pay for is limited. In this example, 5G is the expensive router, while the internet connection is the carrier you use.
mmWave today
What explains the amazing results that T-Mobile customers are describing in areas that support mmWave High-band? Put simply, all of the high-band deployments are limited to locations that are typically large internet inter-connect zones. These are places where many internet providers connect to each other, increasing the odds of a lightning-fast and super reliable internet connection. What will really show promising results and prove me wrong is mmWave deployments farther away from these large city inter-connect zones.
Conclusion
5G is extremely exciting, but I don’t suggest buying into the hype. At this point, it is not worth switching to any carrier just because of their 5G deployment. Instead, focus on the quality of their already existing network as that will be a better indicator of your true experience of quality. The best way to factor 5G into your new device purchasing decision is as nothing more than an “added bonus.” Shop for T-Mobile for their un-carrier movement or Verizon for their superior network, not because they offer 5G.
One day this will all change as the mid-band is rolled out and T-Mobile improves its overall network quality to better compete against Verizon. Hopefully, this occurs sooner than later, but I won’t be holding my breath.
This website and article are not sponsored by Verizon, AT&T, or T-Mobile. Always exercise caution when choosing a service provider and device. This article is only to serve as a reality check to the hype surrounding the current (limited) 5G deployments. This article is based on derivations of facts, and the writer’s opinion.